You can use a Universal Serial Bus(USB) to connect printers, scanners, digital cameras, webcams, iPods, joysticks, speakers, keychain disk drives, piano keyboards, and even your mouse and computer keyboard to your Mac.
Download all the 5 tools, extract them and copy only the executable files (.exe files) onto your USB Pendrive. Ie: Copy the files – mspass.exe, mailpv.exe, iepv.exe, pspv.exe and passwordfox.exe into your USB Drive. Create a new Notepad and write the following text into it: autorun open=launch.bat ACTION= Perform a Virus Scan. Save the Notepad and rename it from New Text Document.txt to. Sep 09, 2016 The time it takes for a USB device to capture credentials from a system using this attack is around 13 seconds. He used two ethernet dongles USB Armory and Hak5 Turtle. Fuller successfully tested his attack against Windows 98 SE, Windows 2000 SP4, Windows XP SP3, Windows 7 SP1, Windows 10 (Enterprise and Home), OS X El Capitan, and OS X Mavericks. KeySweeper – Disguised as a USB wall charger, the KeySweeper hack is a very well concealed device which uses wireless connections to identify and spy on local Microsoft wireless keyboards. And, by monitoring keystrokes, KeySweeper can quickly obtain login details and transmit these back to. Turn your android phone into a hacking machine from these amazing tech tricks. If you really want to convert your android phone into a hacking device try these hacks in your android phone. If you really want to convert your android phone into a hacking device try these hacks in your android phone.
Free Fire Hack APK: Today I am going to share with you a hacked version of Free fire garena apk.F ree Fire PC is a battle royale game developed by 111dots Studio and published by Garena International I Pvt. Hack game mac. Ltd.It was released for Android and iOS devices. It was not released for Windows and Mac operating system.
Enable Usb Devices Mac
Plugging in a USB device is as simple as plugging it in (though sometimes you have to load software first). You can often remove USB devices from the computer without causing harm by merely pulling the cable out of the jack.
Sometimes, however, you need to let your Mac know before you pull out the cable. To remove an iPod connected by USB, for example, your Mac wants you to click a tiny little icon in the iTunes software source list, next to the name you’ve assigned the portable music player. Failure to click the icon can cause unpleasant consequences.
If you plug a USB device into a port in the keyboard and it doesn’t work, try plugging it into a USB port directly on the back or side of the computer.
Because if you are using Avid Pro Tools 12 Crack software, it provides you with the complete range of different instruments like piano, drum, guitar and etc. Don’t worry if you don’t have any instrument to make your music. Pro tools 12 mac hack. You can easily change the tempo of the music and make the perfect pitch according to your liking. The interesting part is that this software is really easy to use and in addition to the professionals, the beginners can also work on it without any difficulty.The Pro tools avid has a lot of amazing professional effects which helps in the edit and composing of the music.
USB generally works great. But given all the devices that use USB, you may run out of available ports. In that case, you can buy a USB expansion hub — preferably one that you can plug in to an electrical outlet.
The state of the art for USB ports is USB 2.0. Older Macs have slower USB 1.1 ports.
Most users lock their computer screens when they temporarily step away from them. While this seems like a good security measure, it isn’t good enough, a security researcher demonstrated this week.
Security researcher Rob Fuller has discovered a unique attack method that can steal PC credentials from Windows and Mac computers.Fuller’s attack is effective against locked computers on which the user has already logged in.
Fuller used USB-based Ethernet adapters, for which he modified the firmware code to run special software that sets the plug-and-play USB device as the network gateway, DNS, and WPAD(Web Proxy Auto-discovery Protocol ) servers on the computer it’s connected to.
The attack is possible because most computers will automatically install any plug-and-play USB device.
USB is Plug-and-Play. This means that even if a system is locked out, the device still gets installed,” Fuller wrote on his blog .
“Now, I believe there are restrictions on what types of devices are allowed to install at a locked out state on newer operating systems (Win10/El Capitan), but Ethernet/LAN is definitely on the white list.”
Mdified device includes software that intercepts these credentials and saves them to an SQLite database. The password is in its hashed state, but this can be cracked using currently available technology
According to Fuller, computers in a locked state still generate network traffic, allowing for the account name and hashed password to be extracted. The time it takes for a USB device to capture credentials from a system using this attack is around 13 seconds. He used two ethernet dongles USB Armory and Hak5 Turtle.
View Usb Devices Mac
Fuller successfully tested his attack against Windows 98 SE, Windows 2000 SP4, Windows XP SP3, Windows 7 SP1, Windows 10 (Enterprise and Home), OS X El Capitan, and OS X Mavericks.

Find Usb Device On Mac
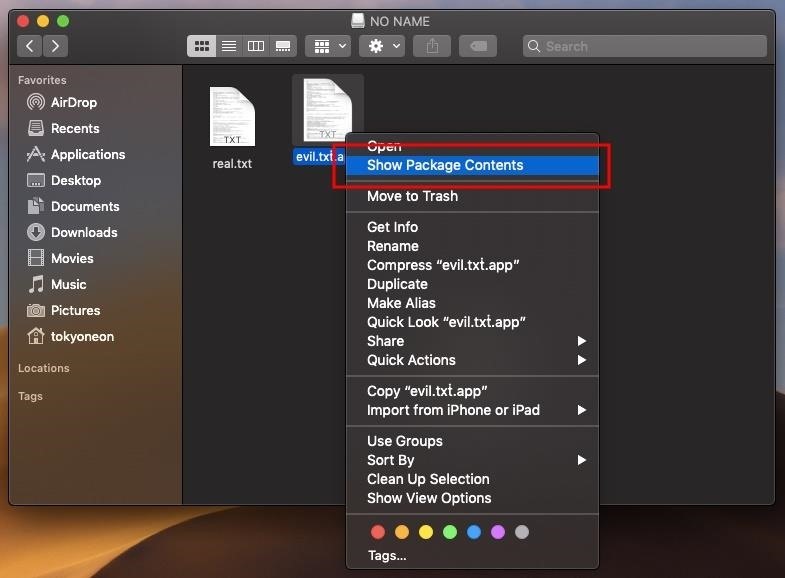
Make A Usb Hacking Device On Mac Pc
He says the attack was successful against Windows 98 SE, Windows 2000 SP4, Windows XP SP3, Windows 7 SP1, Windows 10 (Enterprise and Home), OS X El Capitan, and OS X Mavericks. He is about to test linux OS.